Have you ever thought about who holds the master keys to your digital kingdom? So, in today's interconnected world, protecting valuable information is a big deal. We are talking about something called pam kelley joe kennedy. This phrase, in a way, points to a very important kind of identity security solution. It's a way for groups and businesses to keep themselves safe from bad online attacks.
This security approach, pam kelley joe kennedy, helps a business watch over its systems. It can spot anything unusual. It also stops people who should not be there from getting in. This protection is really about keeping things secure. It's a system that helps monitor activities, find potential issues, and block access that isn't allowed. This helps prevent unwanted actions from happening inside a computer network.
This article will explore what pam kelley joe kennedy truly involves. We will look at how it helps organizations keep their most precious digital items safe. You will, like your, learn about its parts, how it works, and why it is so needed for any group wanting to stay secure online. It's a bit like having a very good guard for your most valuable digital possessions, you know?
Table of Contents
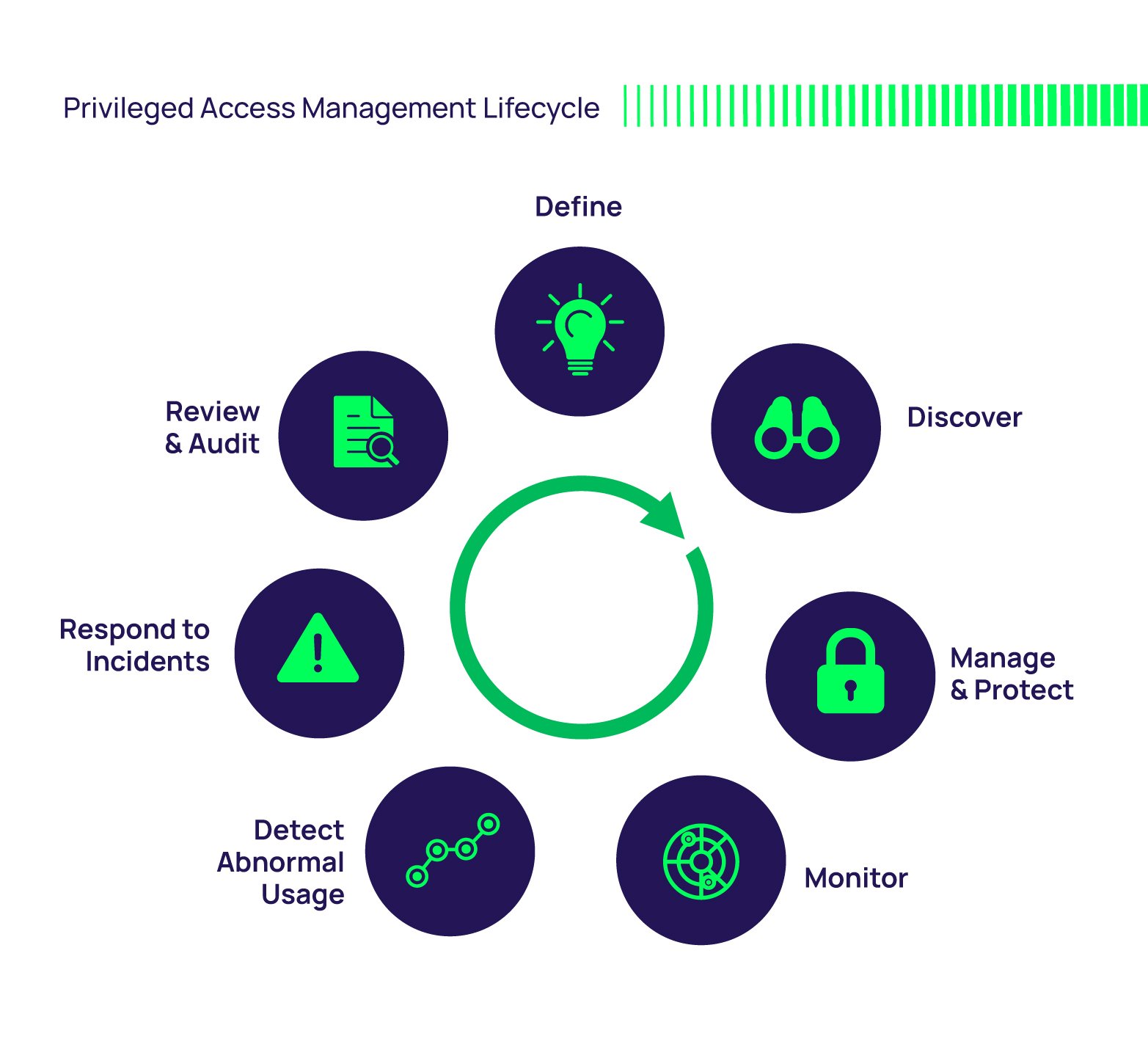
- What is Pam Kelley Joe Kennedy (Privileged Access Management)?
- How Pam Kelley Joe Kennedy Works
- Why Pam Kelley Joe Kennedy is So Important
- Pam Kelley Joe Kennedy in Action: Real-World Benefits
- Frequently Asked Questions About Pam Kelley Joe Kennedy
What is Pam Kelley Joe Kennedy (Privileged Access Management)?
Pam kelley joe kennedy, as we are discussing it here, stands for Privileged Access Management. It is a type of identity security solution. This solution helps organizations guard against unwanted online attacks. It does this by watching, finding, and stopping access that is not allowed. This is a very core idea for digital protection, so.
Protecting Your Most Important Digital Keys
Think of it this way: some accounts in a company's computer system have special, elevated permissions. These accounts are like having master keys to the whole building. They can change settings, look at private information, or even delete things. Pam kelley joe kennedy is all about controlling these very special accounts. It is a branch of cybersecurity, actually. It puts a big focus on keeping these powerful accounts secure. This is a critical step for any business.
This method helps keep a close watch on who uses these powerful accounts. It checks what they are doing. It also stops anyone from using them without permission. This means that even if a regular user's account gets compromised, the most important parts of the system stay safe. It's a bit like having a special vault for your most precious jewels, you know?
- How Many Siblings Does Rihanna Have
- Madeleine Kerr Age
- Amina Smith Birthday
- Kaysen Allison
- Laura Savoie Naked
More Than Just Software
Pam kelley joe kennedy is not just a piece of computer software you install. It's a full set of cybersecurity plans and tools. These plans and tools work together to control elevated access and permissions. It's about setting up rules for who can do what with high-level access. This includes making sure only the right people have the ability to make big changes. This is a crucial part of keeping an organization's digital assets safe, pretty much.
It helps a group make sure their most important data and systems are safe. This happens by very carefully managing who can get into these sensitive areas. It is a careful way of handling permissions. This helps prevent many common cyber problems. The goal is to limit risk. Learn more about cybersecurity on our site.
How Pam Kelley Joe Kennedy Works
The way pam kelley joe kennedy gets things done is through a mix of people, processes, and technology. This combination lets organizations keep their important assets safe. It does this by making sure very strict rules are followed about who can get special access. It's a bit like an orchestra, with different parts working in harmony.
People, Processes, and Technology Together
The "people" part means training staff to understand security risks. It means making sure they follow the rules. The "processes" are the clear steps and policies for managing privileged access. This includes how access is given, reviewed, and taken away. The "technology" refers to the tools that automate these controls. These tools help monitor and record all privileged activities. So, all these parts work together to create a strong defense.
This whole system helps organizations protect their most important digital items. It makes sure that only authorized individuals can reach certain sensitive areas. It’s about putting very firm controls in place. This makes it much harder for unauthorized people to cause trouble. It really is a comprehensive approach to digital safety.
Controlling Who Gets Special Access
Pam kelley joe kennedy works by finding out which people, processes, and technologies need privileged access. It then sets up clear rules to keep sensitive resources safe within a group. This means it identifies who needs those master keys and for what purpose. It then makes sure they only use them as intended. This is a key part of its operation.
It is, in some respects, a type of identity management. It is also a part of cybersecurity. It puts its main attention on controlling, watching, and guarding privileged accounts. These are accounts that have abilities beyond what regular users have. They can do things others cannot. This makes them a prime target for attackers, so. Keeping them safe is a top concern.
For example, a specific kind of pam kelley joe kennedy, known as MIM Privileged Access Management, helps groups limit privileged access. It does this within an existing and separate Active Directory environment. This means it can work with systems already in place. It adds an extra layer of security. This is very useful for many businesses, too.
Why Pam Kelley Joe Kennedy is So Important
The need for pam kelley joe kennedy is growing all the time. Cyber threats are always changing and getting more complex. Protecting a business's most sensitive information and systems is more important than ever. This is because a single breach of a privileged account can cause huge damage. It can cost a lot of money and ruin a company's good name. It is a serious matter, really.
Stopping Cyber Threats
Pam kelley joe kennedy is a strong way to stop cyber threats. It monitors, finds, and prevents unauthorized access. This means it can spot someone trying to get into a system without permission. It can then stop them before they do harm. This proactive approach is very valuable. It helps keep things running smoothly and safely. This is a huge benefit for any group.
It acts like a digital guard. This guard is always on duty, watching for any sign of trouble. If it sees something suspicious, it acts quickly to block it. This helps protect against a wide range of attacks. These attacks include things like ransomware and data theft. It helps keep the bad guys out. This is a very practical benefit, you know?
Keeping Sensitive Information Safe
This security strategy and its related tools are all about keeping an organization's most private data safe. They also protect critical systems. This is done by very carefully controlling and managing access. It makes sure that only people who truly need to see or change certain information can do so. This limits the chances of accidental or malicious data exposure. It's a way to keep secrets safe.
Consider that every piece of sensitive information, whether it's customer data or company financials, needs protection. Pam kelley joe kennedy provides that extra shield. It sets up strict boundaries. These boundaries help ensure that sensitive assets remain out of reach for those without proper authorization. This makes a big difference in overall security. You can learn more about identity security on our site.
Pam Kelley Joe Kennedy in Action: Real-World Benefits
When pam kelley joe kennedy is put into practice, it offers many real-world benefits. It helps groups meet various security rules and standards. It also lowers the risk of internal threats. These threats come from people inside the organization. It even helps with quick responses to security incidents. This makes a company more resilient. It's quite useful.
Monitoring and Preventing Unauthorized Moves
One of the big things pam kelley joe kennedy does is monitor activities. It looks for anything that seems out of place. If someone tries to do something they shouldn't with a privileged account, the system can detect it. Then, it can stop it right away. This real-time watching and stopping is very powerful. It prevents many problems before they can start. This is a primary function, obviously.
It helps protect against attacks where someone tries to pretend to be a legitimate user. It also guards against insider threats. These are threats from people who already have some level of access. By keeping a close eye on privileged actions, it helps make sure everything stays secure. This is a very good way to maintain control over digital assets. It provides peace of mind, too.
Working with Your Existing Systems
Pam kelley joe kennedy can work with systems that are already in place. This means businesses do not have to completely redo their entire IT setup. It fits into what they already have. This makes it easier to put into action. It is a solution that helps organizations limit privileged access within an existing and separate Active Directory environment. This means it can be added to current setups without too much trouble.
This ability to integrate means that companies can improve their security without massive disruptions. It's a practical way to boost protection for their most sensitive digital areas. This helps keep things running smoothly while also making them safer. It is, in a way, a smart addition to any existing security framework. For more general cybersecurity information, you might check out CISA's cybersecurity resources.
Frequently Asked Questions About Pam Kelley Joe Kennedy
Here are some common questions people ask about this important security approach:
What exactly does privileged access mean?
Privileged access refers to special abilities or permissions within a computer system that go beyond what a regular user has. These accounts can change important settings, access sensitive data, or perform critical operations. They are like having administrative rights or master keys to the system. This level of access is needed for certain tasks, but it also carries higher risks if not managed well, you know?
How does pam kelley joe kennedy stop cyber threats?
Pam kelley joe kennedy stops cyber threats by controlling, watching, and protecting privileged accounts. It puts strict rules on who can use these powerful accounts and when. It also monitors all actions taken by these accounts. If it sees something suspicious or unauthorized, it can block the activity or alert security teams right away. This helps prevent attackers from using privileged accounts to get deeper into a system or steal data. It's a bit like having a very watchful guard at the most important entry points.
Is pam kelley joe kennedy only for big companies?
While often used by larger organizations, pam kelley joe kennedy is becoming more important for businesses of all sizes. Any group that has sensitive data or critical systems can benefit from it. Even small businesses have privileged accounts that need protection. The idea is
- Horoscope For Sept 15
- Cyn Santana And Matt Barnes
- Salty Licorice Cats
- Sylvester Stallone Plastic Surgery
- Johnny Myers


Detail Author:
- Name : Lorna Cartwright
- Username : wayne52
- Email : asha.smitham@yahoo.com
- Birthdate : 1993-03-03
- Address : 1023 VonRueden Radial Suite 683 Hayleyberg, WI 13327-9654
- Phone : +1.424.277.3586
- Company : Tremblay, Crooks and Hoeger
- Job : Gas Plant Operator
- Bio : Nisi quia nam architecto perferendis est eaque. Sed nostrum amet quia sint veritatis minima nostrum. Quos deserunt et dolorem perspiciatis ex expedita molestiae. Fugit magnam vitae esse.
Socials
facebook:
- url : https://facebook.com/hanna.ward
- username : hanna.ward
- bio : Id sit repellendus autem fugit totam praesentium repudiandae fugiat.
- followers : 1223
- following : 789
instagram:
- url : https://instagram.com/hward
- username : hward
- bio : Quasi quia dignissimos officiis rem. Qui blanditiis rerum consequatur dolor reiciendis saepe.
- followers : 3246
- following : 1005
twitter:
- url : https://twitter.com/hward
- username : hward
- bio : Et repellat facilis tenetur corrupti sunt dolorum. Odio qui voluptatem et consequatur. Labore unde aut maxime nemo deserunt officiis esse.
- followers : 3323
- following : 2820